Easy To Generate
We are a leader in Secure Mobile Communication solutions by industry analysts, independent testing organizations and security professionals.
Easy To Deploy
We provide encrypted mobile solutions that secure the data of government and centralized organizations, as well as private enterprises.
Easy To Operate
For organizations having more specific requirements, we offer mobile device customization options.

Why Customers Choose Us
We live in a digital world, where data has become the most valuable commodity, and the number of parties with the technological means to intercept, monitor, or exploit this data is growing exponentially.
Our goal is to give you the means to navigate this digital space and communicate through mobile without worrying about the security and privacy of your data.
For over a decade, we have been the trusted partner of SMEs, government agencies, and institutional clients, who rely on our technology for securing their mission-critical communications.
Premium services and beyond your expectation
We offer custom-built encrypted mobile devices and supporting infrastructure to institutional and enterprise clients.
World class cyber security tech
Our solutions focus on securing critical communication systems and protecting data-at-rest from sophisticated threats. We also provide additional services, such as security consultancy, customization, deployment, integration, and tech support.
SQLCipher 256-bit AES full database encryption.
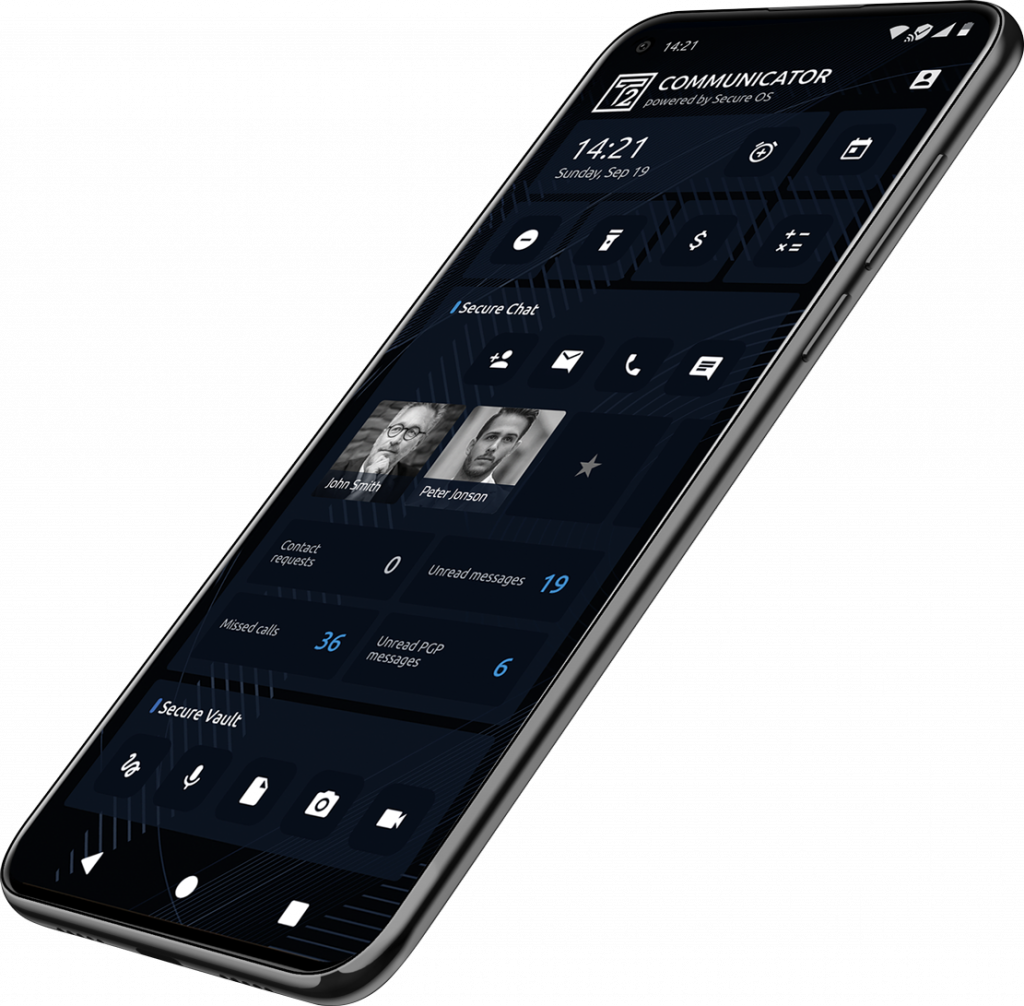
Secure Calendar
Secure Calendar is a private calendar app.
4096-bit RSA key pair used for encryption.
Elliptic curve (ECC) Curve25519/Ed25519.
Voice And Video
Diffie-Hellman key exchange.
SHA-2 hashing used for authentication.