325k
Exposed sensitive files in the financial sector in 2019 alone.
400%
Increase of cyber attacks on law firms since the beginning of the first lockdown in 2020.
42%
Of small businesses identified at least one breach or attack in the last 12 months.
1BIL$
Was the cost of a ransomware attack on Merck and Co., dubbed NotPetya.
Contact us at the Roche Fintech office nearest to you or submit a business inquiry online.
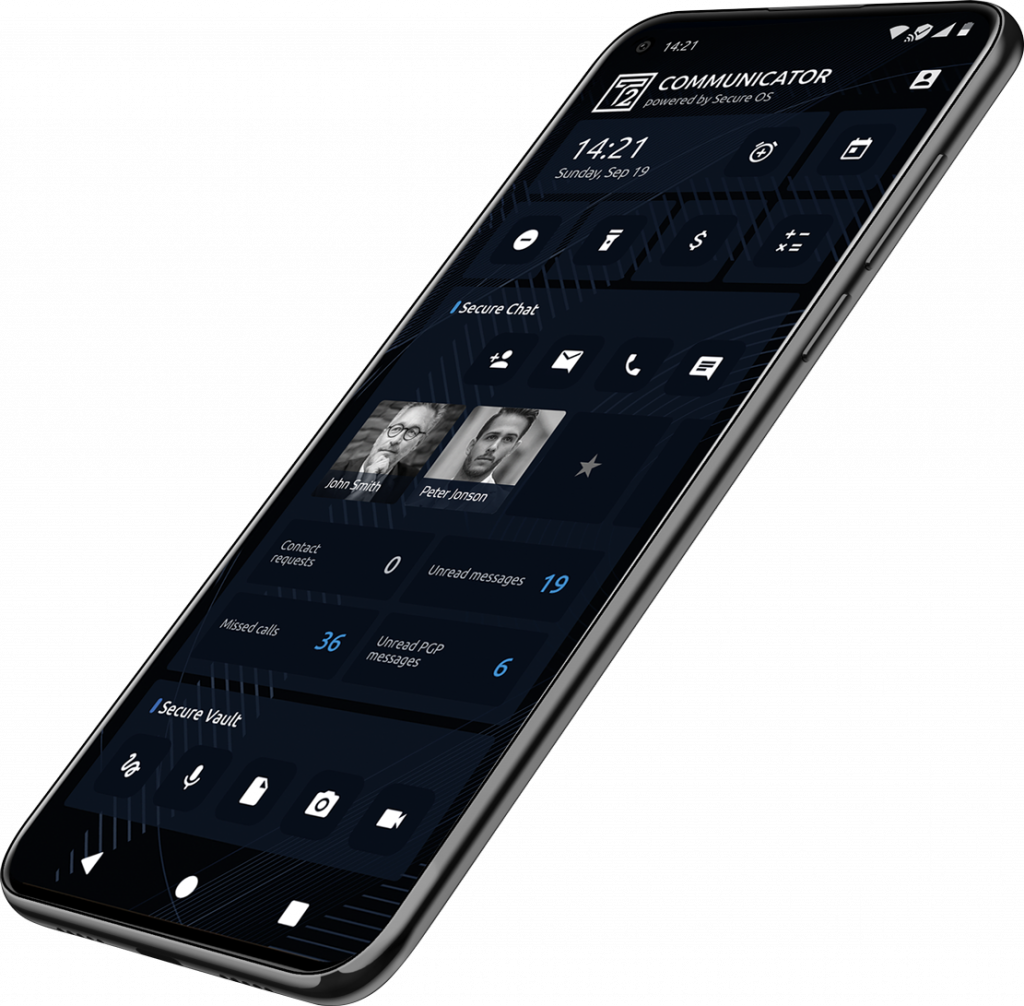
The device has 360-degree protection for any individual or organization. Thanks to the sophisticated encryption, zero-day exploits, malware attacks, phishing, wiretapping, DDoS, MiTM, and online hacking don’t have a chance to succeed.

We live in a digital world, where data has become the most valuable commodity, and the number of parties with the technological means to intercept, monitor, or exploit this data is growing exponentially.
Our goal is to give you the means to navigate this digital space and communicate through mobile without worrying about the security and privacy of your data.
For over a decade, we have been the trusted partner of SMEs, government agencies, and institutional clients, who rely on our technology for securing their mission-critical communications.
Range of Technologies
Secure Operating
System
Secure Hardware
Platforms
Secure Box
Self-Hosted
Secure Administration
System
Decentralized
Infrastructure
Encryption
Scrambling
360-Degree Protection
Attacks against mobile devices are getting more and more advanced. Different parties with malintent can quickly obtain a fingerprint of your device, find vulnerabilities, and exploit them.
To prevent this, we have developed a military-grade mobile OS that is secure on every level.
Strategy development
Multiple levels of encryption
Incoming and outgoing communication is end-to-end encrypted and transmitted over an encrypted network. All data stored on the device is secured and encrypted.
Total Security For Government Enterprise & Individual clients
The T2 Communicator
The device has 360-degree protection for any individual or organization. Thanks to the sophisticated encryption, zero-day exploits, malware attacks, phishing, wiretapping, DDoS, MiTM, and online hacking don’t have a chance to succeed.
Zero-attack-surface;
Verified boot & triple password protection;
Multiple layers of encryption & wipe options;
Secure key store & trusted updates.
Serverless P2P & PGP chat;
Secure PGP group chat;
Secure P2P voice and video calls;
Secure vault (file storage) & calendar.
Complete security-hardened solution;
Numerous quality assurance methods;
A faraday bag and a privacy screen protector;
MDM system, billing system, training, and support.